
Music by Jason Shaw audionautix.com audionautix.com

Music by Jason Shaw audionautix.com audionautix.com
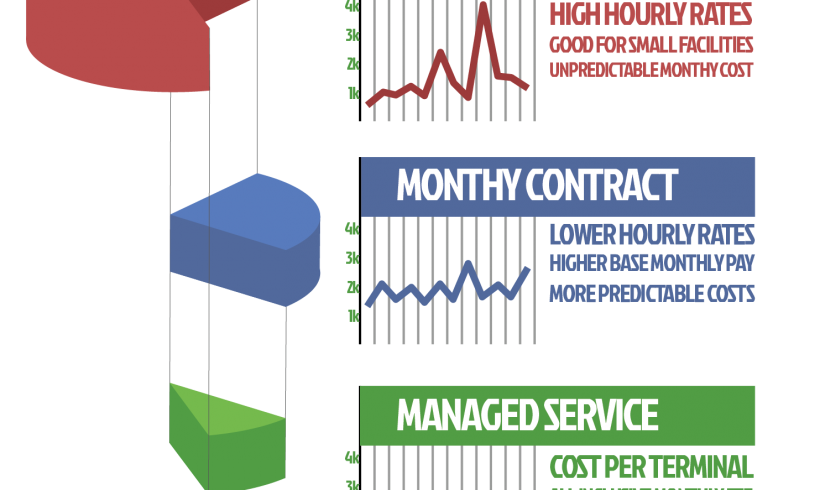
The average skilled nursing facility has a high demand for telecommunications and the use of modern technology. With the use of technology, the need also exists for IT support. While some IT vendors supply support with their contracts on their own software, the computer equipment is often purchased by the facility. There are several options […]

Soon rural long term care facilities will be able to apply for federal funds to help them pay for faster internet. The federal legislation was signed into law by president Obama on June 22, 2016. The law allows Long Term Care facilities to be covered under the S.1916 Rural health Care Connectivity Act of 2015. […]

Save During Daylight Savings! There’s never been a better time to save with HHS Solutions: We are offering the first month of billing free to new clients. Remember daylight savings is this Sunday at 2 a.m.. Spring forward means that 2 a.m. becomes 3 a.m. and, for those who like to sleep in, that means […]

HHS Solutions is running a limited time offer to new customers We are offering a free months worth of billing to our new clients with ongoing support for that month of billing. We are confident that you will find the great value in our services, so we want to offer you a free month of […]

November is home care and hospice month and many caregivers, nurses, nurse aids, and other staff work hard to provide great care to the families and communities that they serve. This is a month of appreciation for a honorable job and the caring individuals that deserve recognition. Try to compliment or thank someone in the […]

It has been a whole month since the ICD-10 changeover. How did everyone fair? The challenges of learning and training employees can be difficult especially with such a significant change. With over 141,000 ICD-10 codes it is impossible to memorize every one of them. Knowing where to start is imperative to getting the correct diagnosis […]

HIPAA security has changed since March of 2013. The new rules change the way everyone deals with electronic Protected Health Information (e-PHI) as well as the networks and vendors the companies use to view and transfer these documents. Under the new rules, you can be fined up to $1.5 Million per year if you are not in compliance, and up to $50,000 per violation. Also now business associates can be held responsible for data breaches and if that were not enough: you now you have to prove that you haven’t had a data breech instead of the opposite. Under the new rules they assume that you have had a security breech unless you can document otherwise. For companies that have policies and procedures for HIPAA that are older than 3 years: You may want to read through your Business Associate Agreements (BAAs) and your policies to make sure the new rules are put into place.
Visit HHS.GOV here for the actual specifications/requirements: http://www.hhs.gov/ocr/privacy/hipaa/understanding/srsummary.html
In short it is important to make sure you are in compliance to these new rules and that your IT vendor/department is aware of these requirements.
 Phishing Attacks:
Phishing Attacks:Phishing is when attackers send you emails or have links in websites that are tailored to look legitimate, but when an unsuspecting person clicks on a link or opens a file within an email it harms the computer. Also, Spear Phishing is an even more targeted attack, in which the hacker gathers info about you to tailor a personalized email message just for you.
 Man in the Middle Attacks:
Man in the Middle Attacks:Man in the middle attacks intercept data between two points and attempt to steal and decrypt the information. This can be done by spoofing a “trusted” network that your device has connected to in the past. You may see this if you are at a hotel and your phone tells you that you are connect to your home network?!?!
 Buffer Overflow:
Buffer Overflow:Buffer overflow is when an attacker breaks a program by giving it too much information (like a really long username). The attacker can then insert code into the website or software that goes where it should not and gain access to a system. This is a high level of attack and difficult to prevent
 Brute Force Attacks:
Brute Force Attacks:Brute force attacks can be very effective against systems that have weak user names and passwords. A brute force attack will try thousands if not millions of usernames and passwords to try to find the right one. More sophisticated attacks use “dictionaries” of the most common passwords to quicken the process.
[cmsms_row data_width=”boxed” data_padding_left=”3″ data_padding_right=”3″ data_color=”default” data_bg_color=”#ffffff” data_bg_position=”top center” data_bg_repeat=”no-repeat” data_bg_attachment=”scroll” data_bg_size=”cover” data_bg_parallax_ratio=”0.5″ data_color_overlay=”#000000″ data_overlay_opacity=”50″ data_padding_top=”0″ data_padding_bottom=”50″][cmsms_column data_width=”1/1″][cmsms_quotes mode=”slider” animation_delay=”0″][cmsms_quote image=”931|http://temp.hhssolutions.com/wp-content/uploads/2015/04/Increased-Cost-not-mean-Revenue-200×200.png|thumbnail” name=”Janet Lytton, R.H.I.T., N.H.A.” subtitle=”Director of Reimbursement”] As I have been working on each of the Facility Statistic files, I have noticed that our facility Medicaid rates have increased very little, if any. This is […]

A person with dementia may be more sensitive to noise. Noise affects people differently from a mild response or catastrophic reaction. Some may have a threshold of a few minutes and others may become overwhelmed after an hour. Each person’s coping style to noise is different. Their individual coping style and personal tolerance to noise […]